Cyber-criminals are no dummies. They saw the cracks in the virtual walls of organizations struggling to support and manage operations—stretched to their limits from suddenly distributed work-forces, disrupted supply chains, and reduced IT budgets. Of course, bad actors dove right in, ringing security alarm bells globally.
The third annual VMware Carbon Black Global Threat Report shows that recent global disruption created new opportunities for cyber-criminals, leading to unprecedented threats. But on the positive side, enterprises do have strategies available to combat rising risks.
Takeaway #1: Cyberattacks Are Increasing Globally
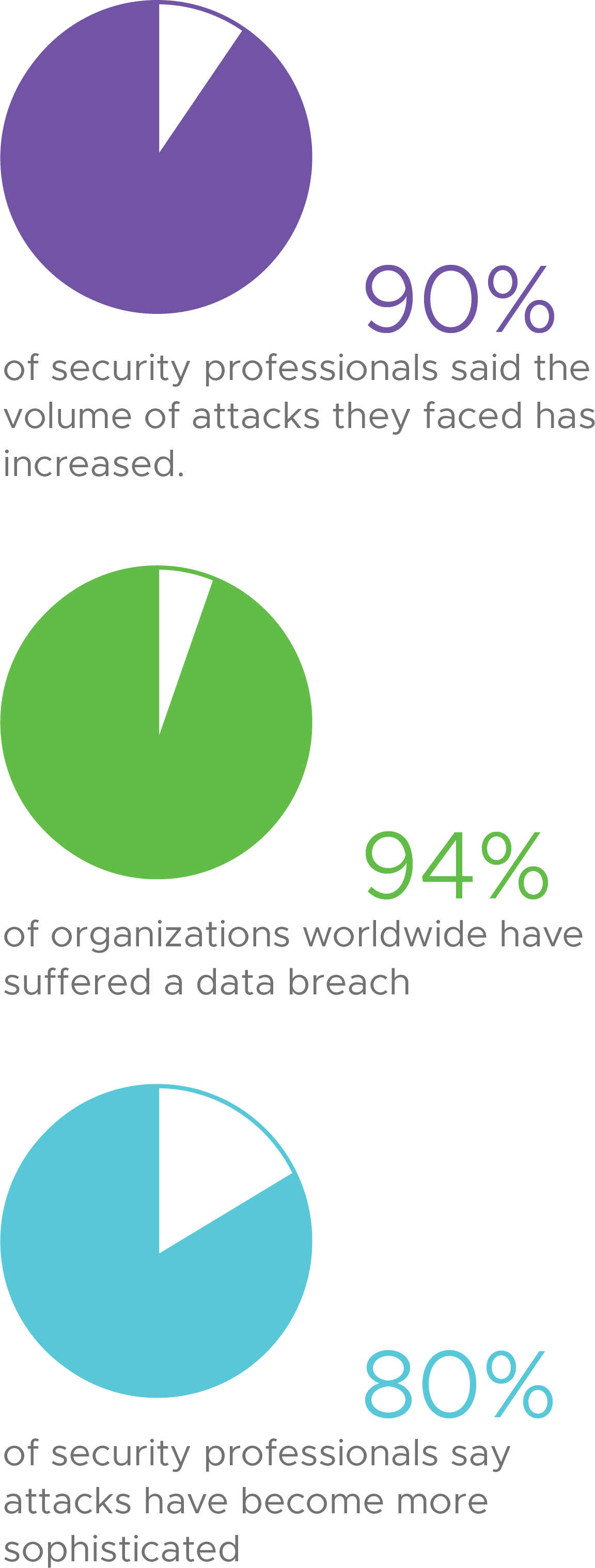
Attackers are innovating and succeeding. Traditional security models are broken. A full 90% of surveyed security professionals say cyber-attacks have increased. With these numbers, not surprisingly, 94% of enterprises worldwide suffered a breach. The average number of breaches reported over the past year was 2.17.
COVID-19 had a decided impact, as coordinated nation-states and scammers alike seized opportunities soon after work-from-home directives were issued around the globe.
More than 9-in-10 security professionals say they saw an increase in overall cyber-attacks as a direct result of work-from-home initiatives.
“With COVID-19, organizations are suddenly faced with the grim reality that they have far less control over their staff’s workplace,” says Dr. Matthew Todd, former CISO and now principal at Full Scope Consulting LLC.
“Many organizations had either no work-from-home plan or it was poorly defined. Suddenly, nearly everyone is working from home using a variety of poorly supported and sometimes personal equipment,” he says. “Staff was not trained for this. IT was not prepared with tools and resources. It’s no wonder that there are gaps in both human and technical security that the bad actors are taking advantage of.”
The biggest problem? Needing to more confidently let users access systems, but being stymied by the inability to institute multi-factor authentication (MFA) swiftly enough. Without MFA, all it takes is one phishing attack exposing employee credentials and the whole system becomes compromised.
Businesses are also having trouble fighting COVID-19-related malware and rolling out software patches in a timely enough manner.
Biggest Shelter-In-Place Security Threats
- Inability to institute multi-factor authentication (29%)
- COVID-19 related malware (15%)
- Inability to roll out timely software patches (13%)
Businesses need to protect enterprise applications and endpoints from the most advanced cyberattacks. They need proven security solutions that leverage behavioral-based security technology capable of collecting and analyzing billions of security events per day.
Takeaway #2: Your Supply Chain Is Vulnerable
Attackers are increasingly targeting smaller companies to “island hop” over to the real target: their business partners. This is how a highly visible attack on a U.S. retail giant unfolded several years ago, and the technique still works today. Attackers used vulnerabilities in the smaller, less-sophisticated company’s security defenses as a point of entry to their much larger and potentially more lucrative partners.
Island-hopping attacks caused 13% of breaches in the last year. This sends a clear message:
When your enterprise assesses its security risks, it’s critical to vet all third-party partners with access to your enterprise data and operating environment.
It’s not uncommon for system maintenance suppliers, such as heating and air conditioning firms, to have access to highly sensitive IT systems.
According to Todd, “Supply-chain vulnerabilities are nothing new. For example, they are specifically called out in the NIST CSF framework. What is new is how the supply chain is no longer a discrete set of suppliers and clients.
“Now, suppliers and clients are part of an organization’s infrastructure, depending on each other in complex and organic ways. This makes risk analysis much more difficult. How much of your infrastructure and operations are not under your direct control?” Todd says.
The recommendation: Don’t just look at partners’ security products. Evaluate their approaches. Do they have a zero-trust, least-privileged model? Do they bolt-on security products or build them into the infrastructure so every app, every cloud, and every device is better protected? With the more effective intrinsic security model, security professionals can see everything happening on the network. So, if island-hopping is in progress, they’ll catch it.
Takeaway #3: Security Budgets Are Rising to Combat Threats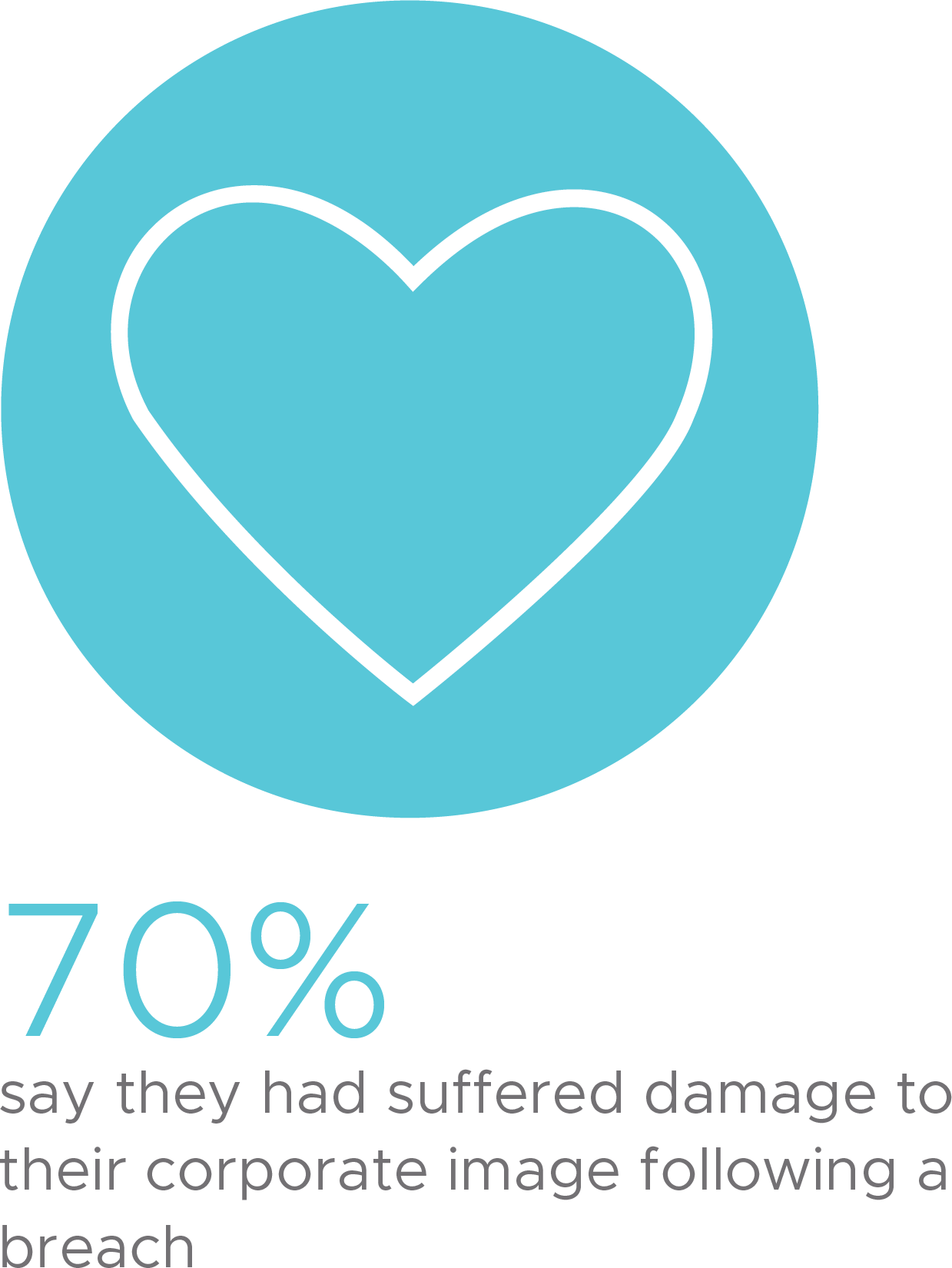
There is now organization-wide recognition that security is critical to not only prevent news-making issues but also to maintain customer loyalty and trust.
That’s likely why security budgets are increasing for 96% of enterprises, even within a general trend of IT budget shrinkage. The average cybersecurity budget increase is 27%, according to survey respondents. These numbers are up from 90% in October 2019 and 88% in February 2019.
“The growing sophistication of attacks and the greater need for integrated, comprehensive, and holistic security is just what I mentioned in my 2020 predictions,” says Todd. “In this report, it’s encouraging to see a greater focus on security as a means to enable the enterprise. I hope that organizations are embracing this at all levels, however, and not simply hoping that increasing the ‘security budget’ will decrease risk.”
Security teams don’t need to invest in new products as on average, they already have almost nine (8.91) security tools. Instead, they need to fundamentally change their approach.

“A Borderless Challenge on a Global Scale”
“What was striking about this edition of our research project was the broad consensus among different countries,” says Rick McElroy, head of security strategy at VMware Carbon Black. “More geographies than ever before reported their highest-ever figures for attack volume increases and subsequent breaches, while budget increases are also at their highest. What this really shows is that cyber defense is a borderless challenge on a global scale.”
Some enterprises have already seen the writing on the wall, modifying their security operations to leverage cloud. They are collecting and analyzing data from the most important security control points: networks, endpoints, identities and analytics. Indeed, customer adoption trends and the Carbon Black Global Threat Report points to enterprises embracing intrinsic security by building security into the digital foundations of their businesses rather than bolting it on.

