March 2, 2020
Effective Cybersecurity Demands A Simpler Approach
by Sanjay Poonen, COO, Customer Operations, VMware
It’s not an overstatement to say that the tech industry is failing when it comes to cybersecurity. One of the core challenges we must address is the reality of disconnected silos. I’m referring here to the siloed nature of the solutions we offer to businesses. A large percentage of breaches are due to misconfiguration and misalignment across the spectrum of security solutions1. But perhaps even more troubling is the siloed nature of the various teams that share responsibility for cybersecurity.
In a typical enterprise, there are numerous teams that “touch” the security challenge on a daily basis, including:
- Risk
- Information security
- Networking
- Device management
- Apps
- Cloud infrastructure
Each team uses their own tools, speaks their own language and has their own version of the truth when it comes to securing apps and data.
It’s up to the tech industry to provide these teams with the visibility, context and control they need to collaborate effectively and secure their environments. The key is a common set of tools that span across apps, networking, devices and cloud infrastructures—all working off of a single version of the truth.
We must recognize that security is a team sport and the cybersecurity solutions businesses rely on day in and day out must be built and delivered with integration as a core principle.
A Frustrating Truth
In our RSAC 2020 keynote, we had the pleasure of talking onstage with Carrie Mills, head of threat intelligence and response at Southwest Airlines. From her vantage point as a security practitioner for 15 years, Carrie spoke to the need for tight collaboration and cross-functional partnership if we ever hope to solve the security puzzle.

“Collaboration across teams is absolutely vital to ensure robust security for the business,” Carrie said.
She then took that mantra a step further, laying out a call to action for security vendors to:
- Drive tighter integration with one other
- Closely collaborate with the businesses that rely on their solutions
I could not agree more.
The frustrating truth is that security today is bolted-on instead of built-in. Most security tools are purchased and installed “after the fact” as a reaction to a new threat or attack. The result is predictable: increased complexity and a reactive mindset across the many teams responsible for security.
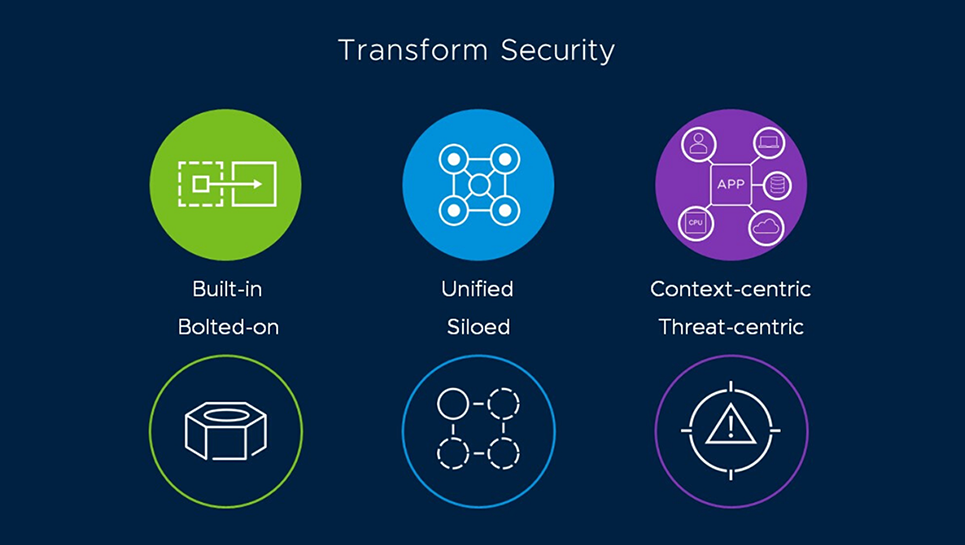
To enable collaboration and a proactive approach, we need to build security into the infrastructure from the ground up and leverage control points around the applications and data we’re trying to protect.
Context-Centric, Not Threat-Centric
There’s an old expression:
You cannot manage what you don’t understand.
The same is true about security. You cannot secure what you don’t understand.
We can never make meaningful progress while we’re ignorant of our applications and the infrastructure that supports those applications. We need far richer visibility and context about our infrastructure, applications and data to really improve security. It effects how we harden systems, align our controls, correlate alerts, investigate and respond.
A Different Approach Is Needed
I believe the security industry is ripe for disruption, resulting in a substantial shift from legacy tools to a newer and simpler platform approach.
We must shift the balance of power from attackers to defenders by enabling collaboration across teams and by removing the complexity inherent in today’s model.
With a security approach that is built-in, teams can coordinate their efforts based on a single version of the truth, taking action and setting policies based on a consistent set of data gleaned from apps, devices and users. With this knowledge, they can be proactive in hardening their environments.
We owe this to the customers we serve. We must equip them to work across the seams and take a proactive approach in order to better secure their apps and data and protect their businesses.
Related:
- VMware Carbon Black “2020 Cybersecurity Outlook” Report Reveals Evolving Attacker Behaviors, Relationship Dynamics between IT and Security Teams
- Download the VMware Carbon Black "2020 Cybersecurity Outlook" Report
- VMware Makes Comprehensive Workload and Network Security More Economical and Easier to Operate Inside Data Centers and Clouds
[1] 2020 Cybersecurity Outlook Report, VMware Carbon Black

